Are regex negative lookarounds possible?
I am trying to filter out a custom inventory using the filter for "matches REGEX". I'm trying to filter using the following:
E\(?!Dom)
however using any sort of negative lookaround results in the page throwing an error. Are negative lookarounds not supported on the K1000 (v6.0) or is there a workaround to this?
I am basically trying to find computers that have non "default" for the custom inventory. All will have the string E\Dom but I want to find the ones with E\ followed by any other string.
----
Edit for clarification.
2 Comments
[ + ] Show comments
Answers (3)
Answer Summary:
Please log in to answer
Posted by:
troyr
9 years ago
@SMal.tmcc
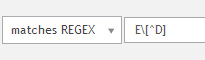
Unfortunately that doesn't work. I wasn't clear in my post in that all computers will have E\Dom. Edited my post to clarify.
So far the closest thing I can do is

However I did find that MySQL doesn't support negative lookarounds, so I'll mark as answered. But if anyone has any other suggestions feel free to post them! =)
Comments:
-
Can you post your CIR and a data sample of it. There may be a method to do it in the CIR itself. If you need all the data in the original CIR you can always create a second CIR that is filtered. I use wmic negative look ups in CIR's alot.
here is one example that looks for startup software not approved by IT.
ShellCommandTextReturn(cmd /c c:\windows\system32\wbem\WMIC.exe startup where "name !='sidebar' and name !='citrix receiver' and name !='tvncontrol' and name !='iastoricon' and name !='apsdaemon' and name !='rthdvcpl' and name !='bcssync' and name !='unity client' and name !='citrixreceiver' and name !='connectioncenter' and name !='ituneshelper' and name !='groovemonitor' and name !='quicktime task' and name !='google update' and name !='adobe arm' and name !='swg' and name !='igfxtray' and name !='hotkeyscmds' and name !='persistence' and name !='lync' and name !='affixa' and name !='AffixaPersonalSettings' and name !='AdobeAAMUpdater-1.0' and name !='Acrobat Assistant 8.0' and name !='F1U201.401' and name !='SwitchBoard' and name !='OneNote 2010 Screen Clipper and Launcher' and name !='SunJavaUpdateSched'" list brief) - SMal.tmcc 9 years ago-
ShellCommandTextReturn(net localgroup Administrators | find /V "The command completed successfully." | find /V "Alias name Administrators" | find /V "Comment Administrators have complete and unrestricted access to the computer/domain" | find /V "Members" | find /V "-------------------------------------------------------------------------------" | findstr .)
Not the most elegant I know.
Sample list from a computer I'm looking for:
Administrator
DOMAINE\Domain Admins
DOMAINE\troyr - troyr 9 years ago-
ahh the good old local admin CIR. I like your approach on this. If you are trying to further filter out your OK domain users/groups can't you just add multiple other find lines to remove them also?
I ended up just calling this as normal. I then run a report exported as csv. I have a macro enabled excel sheet I paste the export into and call 2 search and replace macros, I used the record function to create the macros originally. The macro strips all the garbage text out like you do with your find command. After the first macro runs the sheet lists all the names that are admins. I do this since our laptop users are local admin and can remove our domain groups/users from the admin group. I then run the second search and replace macro that removes all our IT users/groups from the list. I do a data sort, drop the computers with nothing in the admin column, resort by name and save that as a non macro enabled sheet. It takes me a couple of minutes to do.
I am working on a VB script that will run as a kscript on a schedule. This kscript will create 2 files in c:\programdata\dell\kace that will contain just the admin names and admin names minus our IT ones. Then I can do a shellcommand to read those files as CIR's. When I get this done I will post it to this question to share with you. - SMal.tmcc 9 years ago -
Thats a good idea for the kscript. Having a file that contains all local admins and another that has non-default ones. I think that will be way easier for reporting/filtering, worth a shot anyway. - troyr 9 years ago
Posted by:
troyr
9 years ago
An AutoIT script for all local admins (translated from a VB script):
AutoItSetOption("TrayIconHide", 1)
$WshNetwork = ObjCreate("WScript.Network")
$strFilePath = "C:\windows\LocalAdminMembers.txt"
$objFile = FileOpen($strFilePath,2)
$strComputer = $WshNetwork.ComputerName
$objComp = ObjGet("WinNT://" & $strComputer)
$objComp.GetInfo ( )
If $objComp.PropertyCount > 0 Then
$objGroup = ObjGet("WinNT://" & $strComputer & "/Administrators,group")
If $objGroup.PropertyCount > 0 Then
For $mem In $objGroup.Members()
FileWrite($objFile,StringRight($mem.adsPath,StringLen($mem.adsPath) - 8) & @CRLF)
Next
EndIf
EndIf


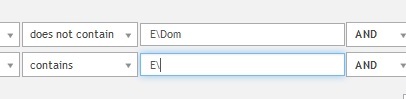

I have seen that link, though I did follow some of the links on there just now and one is to regex for MySQL, which after getting a few more errors, looks like KACE uses. A few of the comments says that MySQL doesn't support negation (using ?!).
Which answers my question but doesn't solve my dilemma =( - troyr 9 years ago